The Password Paradox: Navigating the Identity Crisis in Cybersecurity
by Aaron Flack on Jan 30, 2024

What makes a perfect password?
A unique set of characters, and only used only once? Does it have 36 characters? How about a mix of numbers and symbols? How about something created entirely at random?
In short, the answer is none of the above.
Kicking off our Identity Crisis season, this blog shares actionable insights on fostering cyber resilience around passwords and identity. It's a first in our new series that will bring a suite of ideas on reducing authentication complexity, fostering a culture of cyber resilience, and aligning business practices to common compliance frameworks like Cyber Essentials Plus and NIST.
In a recent survey, we discovered that while individuals typically recall 20-30 online password-protected services they use, the average user manages over 300 password-protected accounts. This poses significant challenges:
- Passwords are reused, repeated, and shared across multiple different platforms
- Users regularly reuse passwords across personal and work applications and services
- Passwords are often straightforward and easy to guess
- People put too much trust in their passwords and do not follow good hygiene rules (changing passwords to critical services regularly for example), relying more on anonymity than secure processes.
Tip 1: Strengthen Password Security Policies in Alignment with Cyber Essentials
Your password stands as the primary defense against cyber threats, and ensuring its robustness is a fundamental step in Cyber Essentials compliance. Take a moment to assess your password against the following common examples - if it resembles any on this list, take immediate action:
- 123456
- 123456789
- qwerty
- qwertyuiop
- password
- password1
- 1password
- 111111
The Cyber Essentials framework emphasises the importance of strong password policies. To align with these guidelines, you’ll need:
- unique passwords for each account avoiding common patterns.
- regular password updates, especially in the aftermath of a phishing, data breach or security incident.
- password management tools which enables secure password storage and retrieval.

In a corporate context, where the use of passwords extends to platforms like Microsoft 365, Slack, HubSpot, Salesforce, QuickBooks, Jira, LinkedIn, Monday, Dropbox, or Box, adhering to the Cyber Essentials framework becomes paramount. It's essential to implement robust password policies and educate employees on the nuances of password security to align with Cyber Essentials standards.
Cyber Essentials Plus certification requires a higher level of assurance, for example, urging organisations to think past just two-factor authentication, 2FA.
By aligning your password practices with Cyber Essentials, you not only enhance your organisation's security posture but also contribute to supply chain security and to a broader cybersecurity framework that safeguards against evolving cyber threats.
Tip 2: Protect Against Password Reuse
Password reuse is a significant challenge most businesses face, due in part to password overload. In truth, no individual could remember over 300 unique passwords.
In an ideal world, the concept of passwords would be obsolete. However, until that day comes, we have to defend our businesses against users reusing (or sharing) their passwords across platforms and services.
A tool like 1Password is our recommendation for this kind of functionality. This secure Password Manager is easily deployed to devices and easy to learn and use.

Users can add an endless catalogue of unique credentials, identities, payment cards and even documents which are private only to them.
It allows administrators to create special shared password vaults for shared services, and most importantly, it is all accessed by only a single Master Password.
Without the burden of remembering 20-30 sub-par unique passwords shared across hundreds of services, each user only needs to remember one highly secure password.
Other security features include 2FA sign in to 1Password, biometrics, passkey support and the need for a “secret-key” only accessible to one already logged in to 1Password to log 1Password into new devices.
1Password also gives you actional insights and intelligence on improving your password catalogue, showing resued passwords, weak passwords, and services which use passkeys or 2FA.
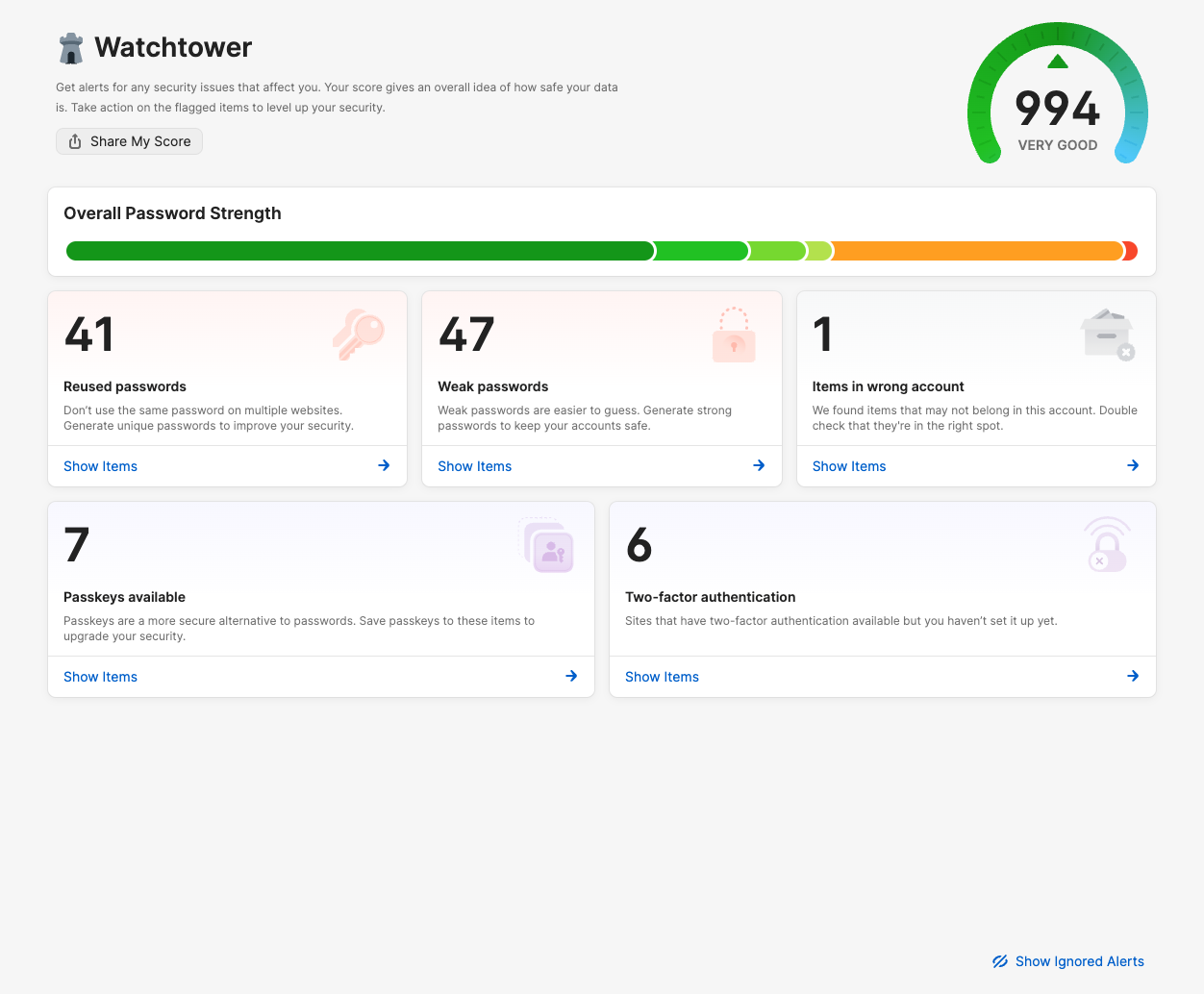
All in all, using 1Password is far more secure than most other password keychain tools mostly due to its flexibility and integration into multiple browsers', OSs and mobile devices. If users save their passwords to their Google Chrome password manager, that password is only available there, not much use if they are using a different browser or device.
Tip 3: Explore new ways to authorise and authenticate user access
There are many options available to businesses who currently use passwords, and the good news is that moving beyond them helps establish a renewed focus on security and vulnerability.
The simplest way, which offers good levels of protection and security, is to adopt a Single-Sign-On platform (SSO), that uses Security Assertion Markup Language (SAML), OAuth, and Multi-Factor Authentication (MFA).
At Conosco, we offer a few solutions for this, but the one we use ourselves is OneLogin, a real innovator in enterprise identity management. It's a leading SaaS solution for managing permanent and temporary internal and external users across all devices and applications and can even extend to BYOD (bring your own devices).

OneLogin’s cloud identity management platform provides more than 2,000 customers with secure single sign-on, multi-factor authentication, user provisioning and more. It can integrate with your directory infrastructure such as Active Directory or LDAP (your central database of users and infrastructure), or act as its own LDAP for smaller organisations or start-ups.
Adopting an SSO is just the first easy step to achieving a passwordless environment. If you are looking at adopting zero-trust principles also, this is also a great step to take.
Tip 4: Adopt Passkeys
The traditional approach to password management is undergoing a paradigm shift, and passkeys are at the forefront of this evolution.
Unlike conventional passwords, passkeys bring a new level of sophistication and security to the table, presenting a revolutionary authentication method that goes beyond traditional password systems' limitations.
Passkeys are tokens that replace or augment passwords for user authentication.
They act as a cryptographic key, providing a unique and secure access method. This innovative approach aligns seamlessly with the security principles outlined in Cyber Essentials and ISO 27001, offering organisations a robust solution to enhance their overall cybersecurity posture.
Adopting passkeys is a strategic move for businesses seeking to bolster their security framework. To integrate passkeys effectively, organisations can start by conducting a thorough risk assessment to identify critical vulnerabilities and understand where passkeys could provide a more secure alternative to traditional passwords.
.png?width=330&height=211&name=Untitled%20design%20(29).png) Managing passkeys involves implementing a secure generation, distribution, and storage system. Businesses can utilise dedicated passkey management tools or services that adhere to industry standards.
Managing passkeys involves implementing a secure generation, distribution, and storage system. Businesses can utilise dedicated passkey management tools or services that adhere to industry standards.
Regularly updating passkeys and ensuring their confidentiality are crucial aspects of effective management.
This approach enhances security and aligns with the systematic control and monitoring requirement outlined in ISO 27001.
Adopting passkeys offers several advantages for businesses.
- They provide a higher security level than traditional passwords, reducing the risk of unauthorised access.
- Passkeys are less susceptible to common password-based attacks, such as brute force or dictionary attacks, enhancing an organisation's resilience against evolving cyber threats.
- Passkeys contribute to a smoother user experience, eliminating the need for users to remember complex passwords or frequently change them.
Conclusion
Passwords are common, and not currently declining. But the rise of cyber-attacks and the challenges for maintaining your own and your business security, is still one of the biggest vulnerabilities. Consider taking immediate action to eliminate passwords wherever possible.
The cost of deploying solutions like OneLogin or 1Password is generally affordable and not only makes it easy for employees to stay secure, but it’s also easily justifiable against the cost of a breach and goes some way to helping you achieve cybersecurity insurance.
Setting up good password hygiene and shifting organisational culture towards cyber resilience is the cornerstone to moving towards a passwordless environment. You can cultivate a responsible cyberculture in this blog.
If you have any questions about the topics discussed or if your organisation is interested in seeing, trialling, or discussing 1Password, OneLogin or any other solution mentioned, please fill out the form below.
You May Also Like
These Related Stories

October Cybersecurity Awareness: Protecting your business from the inside out
Cybersecurity is a central component of every business’s strategy. From securing internal networks to managing third-par …

Unlocking Identity with the Power of the Passkey
A major shift in identity access and management is underway, and it goes by the banner of the passkey. This innovative a …

Risk vs reward: balancing cyber budgets for the next financial year
Depending on the start of your financial year, most businesses should be well into their financial planning by now, with …
