How to Protect Your Business From a Cyber Security Attack
by Conosco on Dec 15, 2020

Written by Hylton Stewart, Head of Security at Conosco
Cyber security threats continue to rise, with trends over the last year showing significant increases in ransomware and phishing attacks specifically. The shift to remote working has contributed to the risks faced by businesses of all sizes, and attackers have been quick to adapt to new opportunities.
However, the basic ways of protecting your business from cyber attacks have remained largely the same.
Why your small or medium business is not safe from cyber attacks
Many small to medium business owners and directors are confident that their businesses will not be the victim of cyber attacks. After all, surely attackers will not actively be targeting your SME when there are so many large companies to target?
In fact, 81% of all cyber security breaches happen to small and medium-sized businesses and historically one small business in the UK is successfully hacked every 19 seconds, according to Hiscox. This is largely due to the fact that businesses in the SME segment are often unprepared, which makes them highly vulnerable. They normally do not have the budget to hire in house security staff or invest in defensive cyber security measures, and attackers know this, meaning they are actually more likely to suffer a data breach or business-impacting cyber attack than a larger enterprise.
With data breaches costing UK enterprises an average of $3.88 (£2.92) million per breach, according to IBM and Ponemon’s Cost of a Data Breach study, a cyber attack could be potentially crippling for a small business. In this piece, we cover everything you’ll need to understand, to help you protect your business from a cyber security attack.
So, what can you do to protect your business today?
- Implement policies and complete risk assessments
- Start with good cyber hygiene practices
- Staff security awareness is critical
- Ensure you have visibility into your IT Estate

1. Implement Policies and Complete Risk Assessments
All good security practices should start at the business level, taking into account the business objectives as well as the actual risks faced. This prevents organisations from overspending on the latest security software solution while failing to deal with the more urgent risks.
Start with a risk assessment and document the results in a risk register. You may want to consider enlisting the help of Managed Service Provider (MSP) as risk assessments can be complicated and time-consuming. Once completed it will form the basis of your security policies and will need to be updated at least annually. As your business matures, try to expand the risk register to encompass more than just IT and security risks, including business-level risks as well.
A risk assessment should:
- Include a data audit (how is data collected, stored, processed)
- An audit of your entire IT infrastructure
- Identify potential threat sources and events
- Identify gaps and vulnerabilities in security and how they might be exploited
- Identify the likelihood that a cyber attack could happen
- Identify the impact on the business
- Identify the risk to the rest of the organisation
Once you’ve complete your Risk Assessment, create a central business cyber security plan – one that supports your business goals and is based on your risks. This can be high level but should be detailed enough to allow for decision making on areas of security spending, and also should be clear enough to support staff awareness of their responsibilities. Make staff aware of this policy regularly and ensure they adhere to it.
2. Start with general good cyber hygiene practices
Once you have assessed your risks and documented a security policy, you can move on to the foundational protections. This stage is a crucial step to understanding how to protect your business from a cyber security attack. Good basic cyber hygiene principles can still greatly reduce the risk of a successful cyber attack against your business and limit the costs – both financial and reputational – if one does occur.
Make sure you have these cyber security basics covered.
- Updates – ensure that you are applying operating system and application patches when they are released, preferably within 30 days for general updates and within 14 days for critical security updates released by vendors. Ideally, this process should be centrally managed and controlled.
- Backups – maintain regular backups of your critical information and systems. This will assist in recovering in the event of a ransomware attack or other loss of data.
- Staff awareness (see more below) – staff remain the first line of defence for any business, and it is a good idea to ensure they have regular security awareness training to enable them to protect your critical information.
- Business Continuity / Disaster Recovery (BC/DR) plan – document a BC/DR strategy to plan how your business will continue to operate during a disaster, from a server outage to a full-scale ransomware attack, and do it before you need it. Test this at least annually, even if it is just a tabletop simulation exercise. Having a plan and not testing it is a sure-fire way to discover the failings in your plan at the worst possible time.
- Anti-malware specific software – Basic anti-virus is no longer sufficient to protect businesses against advanced modern threats, make sure you have a solution on your servers and workstations/laptops that is designed with malware in mind. This can catch many threats before they have a chance to do significant damage
- Set up Web & Email Filters – the vast majority of threats and attacks against businesses are delivered through email these days, not to mention simple spam emails, which can be very time-wasting. Having an email filtering solution in place to stop the majority of spam, phishing and malicious emails before they get to your staff’s inboxes will greatly reduce the chances of a security incident. According to one report, 97% of users cannot identify a sophisticated phishing email. For additional protection from malicious links in advanced phishing emails, a web filtering solution will protect your staff from accidentally accessing a malicious website or downloading ransomware by clicking on seemingly legitimate links.
- Encrypt sensitive data – encrypt sensitive data on all mobile and removable devices, as well as servers (both physical and cloud) wherever possible. Enforce this encryption on corporate mobile devices using a Mobile Device Management solution. This will ensure that even when your sensitive data is stolen, it remains useless and unreadable to attackers.

3. Staff security awareness is critical
Educating your staff on cyber risks and attacks will go a long way to assisting them in protecting your business assets as well as performing their daily jobs with confidence, instead of having to double-check every email they look at and second guess themselves.
Some good basic security awareness topics to make sure your staff are aware of include:
- Avoiding public WiFi: Make sure your employees know it’s against company policy to use public WiFi and provide alternatives such as a mobile private network or VPN for them to utilise when they’re not in the office. Use mobile device management on company-owned devices like work laptops or mobile phones to prohibit users from connecting to public WiFi networks.
- Good password practices: Both how to create good, strong passwords, as well as password reuse risks and forbidding password sharing.
- Phishing awareness: Phishing accounts for by far the single largest malicious attack delivery method, and phishing emails continue to get harder to spot. Provide staff with training on what to look out for, as well as ensuring they have good internal processes to follow to check the validity of emails containing links or requesting actions (such as financial payments).
Use a solution to deliver security awareness and general data protection training to staff, one that allows for tracking and reporting of completion so that you are able to provide evidence of staff training measures should you ever suffer a data breach. Ensure that training is provided regularly, at least annually if not 6 monthly to keep it fresh in your staff’s minds.
4. Visibility is key to protecting your assets
53% of IT leaders are concerned that limited visibility of endpoints will leave them open to a cyber security attack. Once you have the basics in place, it is time to consider the visibility of your IT and information estate. Will you be able to tell when a malicious attacker has breached your network, or gained access to a corporate mailbox? Do you know what devices are connected to your office network, or which accounts are accessing your data in the cloud?
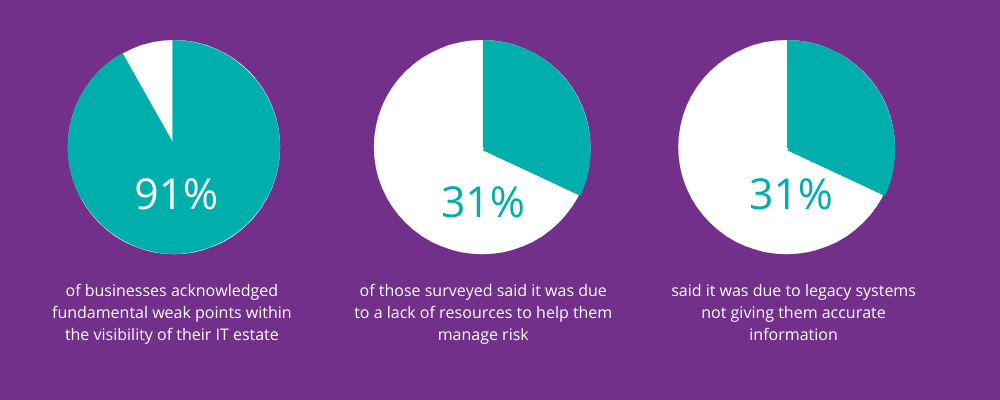
Visibility into your IT and cloud estate is an important step on the journey to security maturity, helping to limit the time that malicious attackers are able to have access to your assets before being detected, thus limiting the damage they can do and the information they can steal. Research by Tanium showed that a huge 91% of respondents acknowledged fundamental weak points within the visibility of their IT estate. 31% of those surveyed said it was due to a lack of resources to help them manage risk and a further 31% said it was due to legacy systems not giving them accurate information.
Endpoint Detection and Response (EDR) and Security Information and Event Management (SIEM) solutions can help prevent cyber attacks by providing visibility and monitoring, as well as incident detection and response capabilities to reduce risks and limit the potential damage of an attack. These solutions require skilled and dedicated staff to monitor and operate them, therefore many businesses will turn to an outsourced Security Operations Centre (SOC) to help them monitor and respond to alerts.
Get the basics right, then add layers
A good defence against malicious attacks and protection from data breaches requires a layered approach to cyber security, there is no single solution or action that will protect your business 100% of the time. Start with a good foundation and then layer on additional defences to cover risks and gaps in existing protections and mitigations. This will ensure that your risk of a successful cyber attack is lower and that when an attack against your business does succeed, which one will eventually, you are able to resolve it quickly and limit the damage.
If you have any questions about information security or need support protecting your business from cyber attacks, do get in touch with one of the experts at the Conosco Security Division: securitydivision@conosco.com
You May Also Like
These Related Stories

Spear Phishing – All You Need To Know – Conosco
Information and Cyber Security should be a top priority for any business, but a large number of companies are vulnerable …

A guide to cyber insurance in 2025
Mid-sized UK businesses have seen a continued rise in cyber threats over the last year, with more data emerging from 202 …

How London’s IT leaders can prevent a ransomware attack
Ransomware is on the rise. How can IT support departments and business owners prevent a ransomware attack and potentiall …
