How to Build a Security-Led IT Strategy
by Conosco on Mar 16, 2021

Written by Hylton Stewart, Head of Security at Conosco
Cyber-attacks continue to rise with 88% of surveyed UK businesses falling victim to a breach in the last year. As organisations strive to maintain the security of their IT infrastructure, businesses must ensure that they have a detailed IT strategy in place.
This is reinforced by the rapidly changing technology landscape and the inception of cutting-edge technology such as artificial intelligence, IoT and 5G which has paved the way for a more connected world. Whilst it has opened up many new opportunities for digital innovation and remote working, it has also allowed malicious attackers to exploit vulnerabilities.
A security-led IT strategy should align with your business objectives as well as your unique risks. It should develop as your business grows and have the agility to adapt to new threats.
In this blog, you’ll discover how to build a security-led IT strategy, including:
- What a security-led IT strategy is
- The key components of your strategy
- What it should include
- The risks associated with not having a security-focussed IT strategy
What is a Security-Led IT Strategy?
An IT strategy is a plan that defines an organisation’s technology investments and the use of IT assets allowing the business to achieve its goals, drive efficiency and add value. It acts as the framework for any decisions and actions taken during a given period and will guide projects and IT spend.
A security-led IT strategy is therefore a strategy that is based around security considerations, however, it is not purely security-focused.
A good security-led strategy starts from a position of awareness of the organisation’s assets, both physical such as laptops as well as informational such as electronic documents and cloud services, and builds a risk profile for the organisation.
Once the security risks are known, they should form the basis of the IT Strategy planning. This will ensure that the strategy supports the security of the organisation’s assets and contributes to developing the cyber security maturity of the organisation over time.
Some larger organisations opt to keep their cyber security strategy separate from their overall IT strategy document, although the two interrelate. This can cause issues – security and IT are so closely intertwined, they should be considered together to ensure the best possible protection for your organisation.
5 Key Components of a Security-Led IT Strategy
To build a balanced IT strategy, businesses must consider existing tools, systems and solutions as well as any improvements or new technology needed to advance the business.
Organisations should begin by taking a holistic view of their IT estate and produce an audit of the assets available. They can then use this to identify gaps in security.
Below are 5 key components to consider when building a security-led IT strategy.
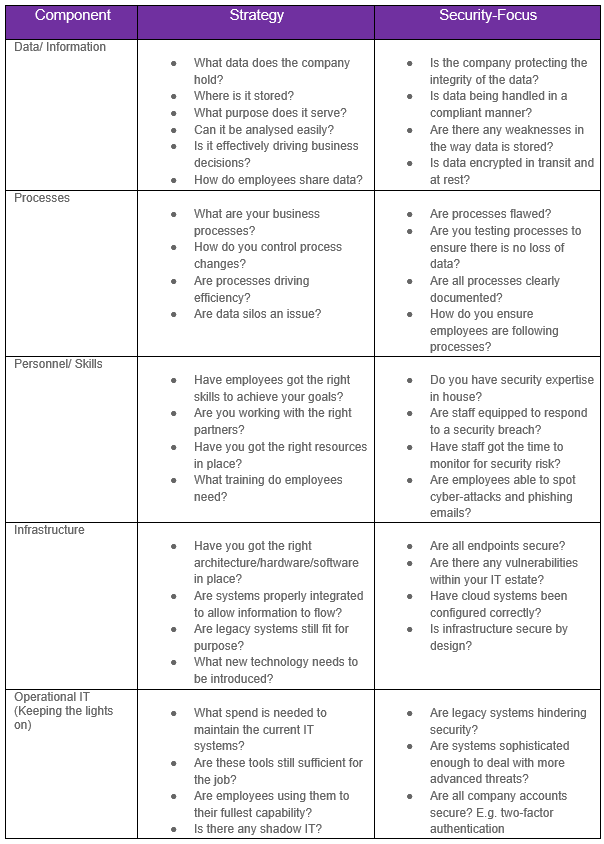
What Should a Security-Led IT Strategy Include?
While the contents of an organisation’s IT strategy should always be bespoke to its needs and based on its risk profile, some elements are always relevant and based on general good cyber hygiene practice.
Top-down commitment
Any IT strategy, and specifically a security-focused one, should always be led from the top of the organisation, and have full commitment from the CEO and Board level. This not only ensures that adequate resources will be available but also sends the right message to the rest of the organisation that security is important. Organisations should have a senior sponsor who is responsible for security, ideally one that reports to the CEO or Board, and not to the CTO.
Roles and responsibilities
In addition to ensuring that sufficient resources are available, it is important to document the roles and responsibilities related to IT and security to ensure accountability and ownership of the various elements as well as to avoid conflicts of interest. This last point is especially important as traditionally IT and security are seen to have potentially conflicting business drivers – IT’s function is to enable the business through technology whereas security’s function is often perceived as limiting what IT can allow. Blending these two areas to better support the organisation requires clear communication.
It is also important for organisations to have a dedicated role for security, as opposed to it being an additional responsibility. For example, some organisations will appoint a Chief Information Security Officer (CISO) or Data Protection Officer (DPO). Where this is not possible they may choose to elicit the help of a Virtual CISO or Virtual DPO.
According to a report by Ponemon Institutes, the average cost of a data breach is $3.86 million. However, by appointing a CISO the average cost decreased by as much as $144,940.
Asset awareness
As stated earlier, awareness of the organisation’s assets is a critical first step in determining the risks faced by the organisation, and therefore the security and IT controls that need to be included in the strategy. The same is true of the organisation’s information (which is also an asset). If an organisation does not know what information it holds, where that information is stored and accessed, and how important it is, it will never be able to adequately protect it from the risk of a breach. This is where the classification of information becomes essential.
Risk-centric
Any strategy related to IT and security should always be designed and driven with the specific risks faced by the organisation front of mind, as opposed to any other driver such as the latest technology or vendor recommendations. This will ensure the effective use of the IT budget to reduce organisational risks.
Privacy by design
The privacy of data should be considered at every point in its lifecycle, regardless of whether it is client data, employee data or operational information. Building privacy controls into all areas of the organisation at the process-level will increase the security of information by default, and assist the organisation in meeting its regulatory responsibilities.
Secure configurations and integrations
Alongside stolen or compromised credentials, misconfigured cloud servers are a leading cause of cyber-attacks. Breaches due to cloud misconfigurations cost around $4.41 million which is nearly half a million dollars more than the average cost. With many businesses quickly changing their IT strategies to incorporate cloud solutions as a result of the pandemic, it is now crucial for organisations to take a look at their infrastructure and remediate risk.
It is also prudent for organisations to consider integrations as part of their security-led IT strategy. Many services are now integrated with the cloud and with an increasing number of IoT devices being connected, it offers a much larger attack surface for cybercriminals and new entry points into an organisation’s network.
Regular review and testing
No strategy or plan is ever a ‘set and forget’ exercise, regular reviews and testing of the strategy using real-world scenarios are vitally important to ensure that the strategy remains fit for purpose.
Organisations should build regular vulnerability assessments and penetration testing into their IT strategy to ensure defences are robust and working effectively. Any weaknesses identified should be fixed immediately and the IT strategy updated to reflect the new security measures.
Continual improvement
Closely tied to the previous point is continual improvement, which most often comes in the form of lessons learnt from either real-world incidents or from testing the strategy. As technology and risk evolve, the strategy needs to be continually improved to not only maintain the same level of protection but to provide better protection in the future.
The risks of not having a Security-Led IT Strategy
A security breach can have a devastating financial and reputational effect on an organisation. Not to mention that any data loss can have a long-lasting impact on business operations.
It is not a matter of if an organisation will suffer a security breach, but when. By failing to incorporate security into the IT strategy you risk leaving IT assets open to attack. When a threat does strike being unprepared may mean you do not have the tools in place to adequately detect and respond to incidents.
Likewise, it leaves room for human error. An organisation’s staff are its first line of defence. If employees are not given guidance on how to protect data and are not trained to spot potential attacks, data could quickly fall into the hands of hackers and systems may become compromised. Not only will this lead to a lack of client trust but it could result in large fines for non-compliance with GDPR and Data Protection Regulations.
A security-focused IT strategy will arm your business with a blend of solutions that will allow you to monitor your environment and remediate risk quickly. From performing a gap analysis to deploying SIEM solutions that detect and alert users about security incidents, only by aligning security with your technology plans can you build a more resilient IT infrastructure.
Round-Up
Failing to plan, document, regularly review and test a detailed security-led IT strategy will greatly increase the risk to your organisation. As technology evolves at a fast pace keeping up with change and developing more sophisticated security solutions that will help you detect and respond to cyber-attacks will become essential to your business.
Conosco’s experts can provide you with the strategic leadership and security expertise to create an IT strategy that gives you the freedom to digitally transform whilst guaranteeing the security of your systems and the integrity of your information.
We will:
- Work with you to align your IT strategy with your business objectives
- Help you identify vulnerabilities and gaps in your security posture
- Provide guidance on security best practice and compliance
- Develop a roadmap for securing your business
- Help you undergo remedial work ranging from configuration changes to selecting and deploying security applications
- Provide security awareness and training
- Continuously monitor your environment via our Security Operations Centre
If you have any questions about the Information Security of your business, do get in touch with one of the experts at the Conosco Security Division: securitydivision@conosco.
You May Also Like
These Related Stories

Spear Phishing – All You Need To Know – Conosco
Information and Cyber Security should be a top priority for any business, but a large number of companies are vulnerable …

What Is True 24/7 IT Support and Who Needs It?
Written by Noel Thompson, Director of Global Support at Conosco Gone are the days of the traditional Monday to Friday, 9 …

What to do when your IT Support starts to fail you
The gap between expectation and reality IT support is meant to underpin performance, not frustrate it. But when service …
