Stop the Smishers
by Aaron Flack on May 22, 2024

Stop the Smishers
7:42
What is smishing?
Smishing is similar to phishing, intending to trick victims into handing over sensitive information that can be used to infiltrate networks or extort money. These attacks use text messages instead of email to reach their targets.
You can now listen to our blogs using the media player above!

With users and organisations becoming wiser and protecting themselves against phishing over email, smishing is becoming a more common attack. People are more likely to click on links in text messages, and with more and more companies adopting bring-your-own-device (BYOD) policies, this is becoming an easier way to infiltrate networks.
Many companies have some form of email management that can automatically blocks phishing attempts, but it’s rare to have the same protection for text messages, especially on non-company devices. Smishing attacks have even taken place over popular messaging apps like WhatsApp, so it’s even more important to understand the risk and take action to protect your organisation.
Examples of smishing
Like traditional phishing, some of the most common smishing attacks attempt to trick the target into thinking they need to follow the link to receive something or continue using a service. For instance, a message regarding a parcel delivery they have missed, a replacement bank or credit card, a password reset, a tax communication, or even a prize win. In one case, Fifth Third Bank customers were targeted with text messages purporting to be from the bank warning them that their accounts had been locked.
When they followed a link within the message to unlock their account, they were taken to a fake version of the Fifth Third website that prompted them to enter details, their usernames, passwords, one-time passcodes, and PIN numbers. Of course, once the attackers had their details, they could withdraw money from their accounts. In less than two weeks, $68,000 dollars was taken using the bank’s cardless ATM function. This continued for a few months with losses totalling over $100,000 before the criminals were apprehended.
You may remember the news last year that Activision (the developer/publisher behind Call of Duty, Overwatch, the Spyro and Crash Bandicoot reboots and many other famous IPs) was hacked by an SMS phishing text.

In December 2022, cyber attackers used social engineering tactics to deceive an Activision HR employee, compromising almost 20,000 employee records. The exfiltrated data contained 16,000 unique email addresses and the affected employees' names, phone numbers, job titles, and office locations. Activision has confirmed that no highly sensitive employee information was included in the breach and considered themselves lucky based on their exposure.
It could have been a lot worse. What if customer data was stolen? What if user passwords were compromised? What if banking data was scraped?
Smishing and 2FA Codes
One of the most alarming and recent developments in the world of smishing is the rise of cases involving the interception of two-factor authentication (2FA) codes
Two-factor authentication (2FA) serves as a digital ‘moat’, offering an extra layer of security to deter unauthorised access. It usually involves receiving a unique code on your mobile device that you must enter to access your accounts. While it's a robust system, it can be vulnerable to potential threats like smishing.

Picture this: you get a seemingly harmless text from your bank confirming a transaction you never authorised. You start to panic. The message includes a link to 'secure' your account. You click it, unknowingly entering your login details on a counterfeit website that mirrors your bank's. Suddenly, you receive a 2FA code on your phone. Feeling relieved, you enter the code, believing you're fortifying your account. In reality, you've just handed the keys to a smisher.
These cyber con artists are sophisticated. They can intercept your 2FA codes in real-time, using them to gain immediate access to your accounts. Once in, they can drain your finances, steal sensitive information, or lock you out entirely. It's like letting a burglar into your house because they claimed to be from the alarm company.
Protecting yourself from smishing and 2FA interception requires vigilance. Always scrutinise unsolicited messages, especially those asking for personal information or directing you to click on links.
4 ways to prevent smishing attacks
Just like phishing, there are some easy ways for individuals and companies to protect themselves against smishing attacks.
SMS filteringMany smartphones and network providers now have features to filter out potential spam messages. Enabling these is an easy way to prevent a significant number of spamming attacks from reaching their target.
The best way for organisations to protect against smishing attacks is to implement a mobile threat defence (MTD) system. It can manage both company-owned and user-owned devices and be configured to give users as much or as little access as needed. It should be set up to automatically apply security policies to any devices that connect to the network, ensuring that operating system updates are applied and all company data is protected.
Watch our video below on defending against smishing when MTD is disabled vs when it is turned on.
Device manufacturers regularly release security updates that fix any potential loopholes that hackers can exploit. However, these are not necessarily installed automatically. Individuals should check that they have automatic updates switched on and organisations should consider some form of mobile device management to ensure updates are applied.
Forewarned is forearmed. Individuals should make themselves aware of the different types of smishing attack and how to spot them. Organisations should offer regular communication and training to advise staff on the types of attack they are most likely to face. They should also have a simple process for reporting any suspicious messages so that they can be quickly investigated.
Adopting robust mobile security into your mobility strategy
Integrating Mobile Threat Defence (MTD), Mobile Device Management/Unified Endpoint Management (MDM/UEM), and mobile telecoms tariffs create a robust defence against smishing attacks. This powerful combination provides comprehensive protection meaning real-time threat detection, centralised device management, and secure SIM oversight.
When a smishing attempt occurs, MTD swiftly identifies and blocks malicious links and suspicious messages before they reach the user. At the same time, MDM/UEM ensures that all devices strictly adhere to security policies, prohibiting the installation of unauthorised apps that could serve as vectors for smishing attacks.
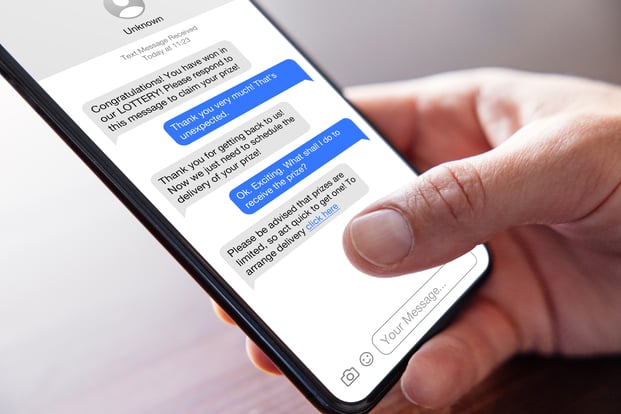
Integrating mobile telecoms tariffs gives organisations monitoring and control of SIM usage, effectively preventing SIM swap fraud, another method often used in conjunction with smishing to intercept 2FA codes. This cohesive defence mechanism guarantees that every layer of mobile communication and usage is safeguarded, significantly reducing the risk of successful smishing attacks and upholding the security of corporate data and user information. Additionally, it removes a lot of the responsibility placed on the individual, too.
Stop the smishers and get a demo on MTD today
Share this
Previous story
← 5 anti-phishing steps to take todayNext story
9 Reasons To Outsource Security Operations →You May Also Like
These Related Stories
Outsourced IT Support for Mid-Sized Businesses – The Facts


Outsourced IT Support for Mid-Sized Businesses – The Facts
IT plays a pivotal role in any business; it empowers your people to do their job, it enables processes to be streamlined …
Jul 13, 2018
2
min read
5 anti-phishing steps to take today


5 anti-phishing steps to take today
Anyone can be the target of a phishing attack. No matter how big or small your company is. No matter which industry you’ …
May 15, 2024
6
min read
Improving Business Resilience with Proactive IT Strategies


Improving Business Resilience with Proactive IT Strategies
Building resilience into your IT and support infrastructure is key to maintaining smooth operations and minimising disru …
Oct 8, 2024
3
min read
